9 Ways to Improve the Security of Your Home Computer

We all want to make our home computers more secure. As many of us are not sure where to start or who’s advice to trust, here are are some tips from a very reliable source: The Department of Homeland Security’s United States Computer Emergency Readiness Team.
How to Land the Best Jobs in Cyber Security [Includes Salary Data]

For job seekers looking for high pay, job security and the option to work in any sector and in any state, the cybersecurity field is the place to be.
The Power of Reverse Engineering in Cyber Security

Reverse engineering is a powerful tool for any software developer. But as with any tool, it’s only as good as the person using it. Understanding reverse engineering and how it can be used is important for new and veteran developers alike. See Previous Article At Cyber Security Online Training
Hacking with Python – 6 best online courses for ethical hackers

If you’re looking to get into ethical hacking, getting acquainted with Python is a great start. We discuss Python and ethical hacking and reveal the best online courses you can take to start training in the field.
10 Cybersecurity Myths You Need to Stop Believing
Cybersecurity is one of the most integral aspects of business in today’s world. Companies have finally started to invest in cyber defense and training. However, despite all of the focus on making businesses cyber secure, there are various misconceptions and myths about Cyber Security Training that should be avoided.
Security Best Practices: Symmetric Encryption with AES in Java and Android
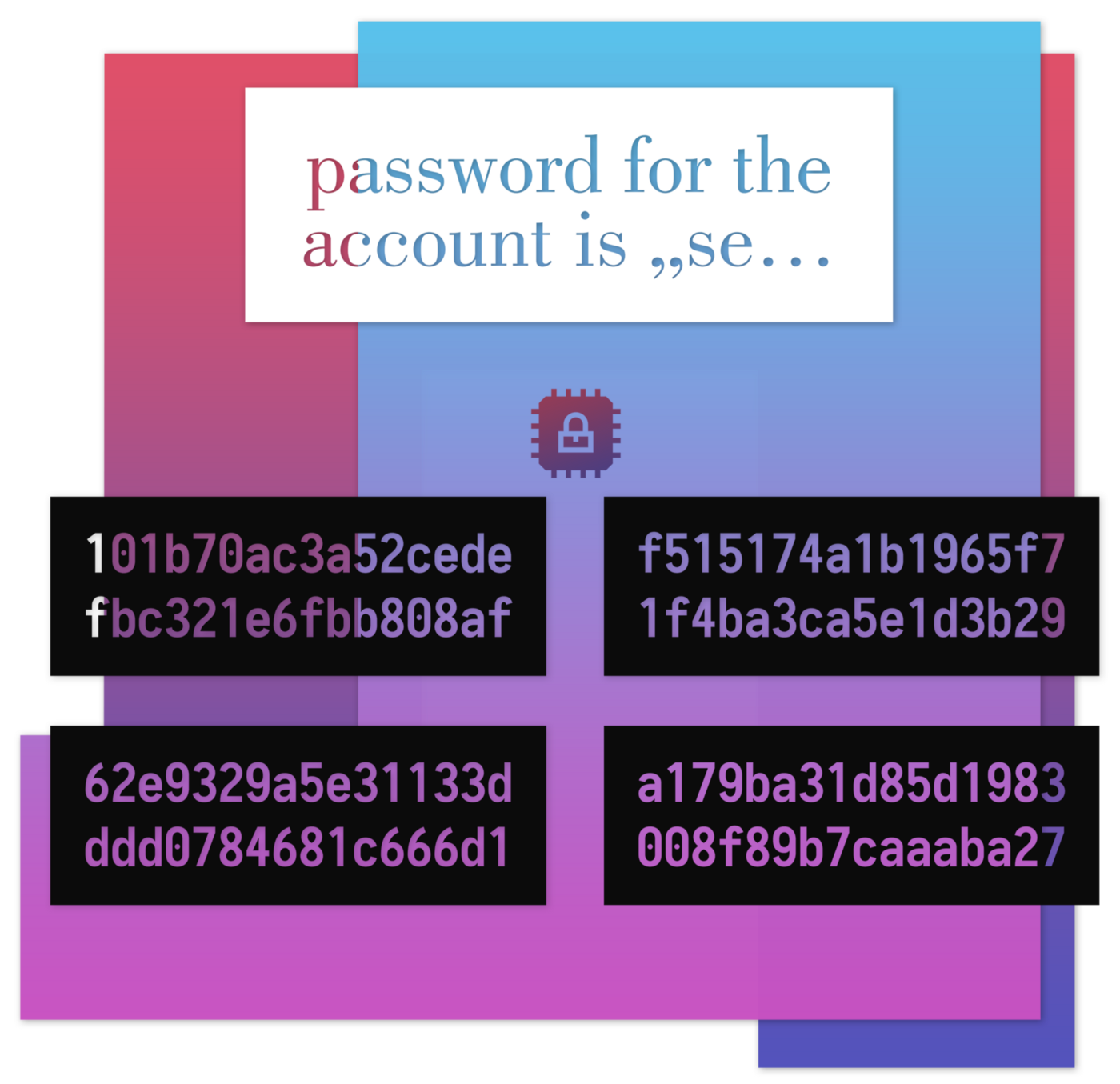
In this article I will bring you up to speed on the Advanced Encryption Standard (AES), common block modes, why you need padding and initialization vectors and how to protect your data against modification. Finally I will show you how to easily implement this with Java avoiding most security issues.
How to Secure Your Security at the Speed of 5G
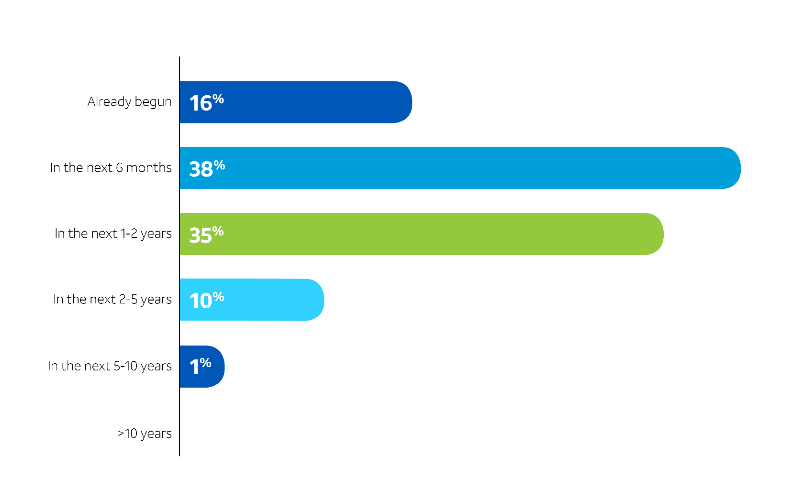
While some enterprises appear to be getting an early jump on the security implications of 5G, many are struggling with the implications to the business and the changing security model. This is based on a survey AT&T Cybersecurity conducted with 451 Research of 704 cybersecurity professionals in North America, India, Australia and UK. Participating organizations spanned 13 industry verticals and each had more than 500 employees.
Is Getting Your Certified Ethical Hacker (CEH) Worth It?

We get this question all the time from IT professionals. They want to make sure that their money and time is going to be well spent. So, is becoming a white hat hacker worth it? The short answer is a resounding, “yes.”
What is application security? A process and tools for securing software

Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps. Much of this happens during the development phase, but it includes tools and methods to protect apps once they are deployed. This is becoming more important as hackers increasingly target applications with their attacks.
Best Tools to Start Pen Testing
A big part of penetration testing is using the right tools. Being able to automate scans, crack passwords, and sniff packets can make you more effective at identifying vulnerabilities.